2025-0240 Continuous Vulnerability Assessment Analyst Support (CTS) - TUE 16 Sep en NATO Communications and Information Agency (NCIA)
NATO Communications and Information Agency (NCIA) · Mons, Bélgica · Onsite
- Professional
- Oficina en Mons
Deadline Date: Tuesday 16 September 2025
Requirement: Continuous Vulnerability Assessment (CVA) Analyst Support for NCSC Assess Branch
Location: Mons, BE
Full Time On-Site: Yes
Time On-Site: 100%
Period of Performance: As soon as possible but not later than 20 October 2025 until 31 December 2025 with possibility to exercise the following options:
• 2026 Option: 1st January until 31st December 2026
• 2027 Option: 1st January until 31st December 2027
• 2028 Option: 1st January until 31st December 2028
Required Security Clearance: NATO COSMIC TOP SECRET
1. PURPOSE
The objective of this statement of work (SoW) is to outline the scope of work and deliverables for the Continuous Vulnerability Assessment (CVA) Analysis for Assess Branch.
The purpose of the work package is to provide support to NATO Cyber Security Centre (NCSC) to fulfil identified Cyber Security Continuous Vulnerability Assessment (CVA) Analyst Support activities more effectively.
2. BACKGROUND
NCIA has been established with a view to meeting the collective requirements of some or all NATO nations in the fields of capability delivery and service provision related to Consultation, Command & Control as well as Communications, Information and Cyber Defence functions, thereby also facilitating the integration of Intelligence, Surveillance, Reconnaissance, Target Acquisition functions and their associated information exchange.
The NATO Cyber Security Centre (NCSC) is a team of over 200 members working to monitor and protect NATO networks. In the NCSC’s role to deliver robust security services to the NATO Enterprise and NATO Allied Operations and Missions (AOM), the centre executes a portfolio of programmes and projects around 219 MEUR euros per year, in order to uplift and enhance critical cyber security services. The Portfolio ranges from Programme of Work (POW) activities funded via the NATO Military Budget (MB) to Critical / Urgent Requirements (CURs/URs) and NATO Security Investment Programme (NSIP) projects funded via the Investment Budget (IB). In some edge cases, projects are also funded via the Civilian Budget (CB). Projects can span multiple years and are governed by various frameworks, including the Common Funded Capability Development Governance Framework (CFCDGM).
In order to execute this work, NCIA is seeking additional support through contracted resources (or consulting) to support the work undertaken by the NATO Cyber Security Centre (NCSC) in the area of Communications and Information System (CIS) security, cyber defence and cyberspace operations. This Statement of Work (SoW) specifies the required skillset and experience. To support NCSC for the execution of tasks identified in the subject work package of the project, NCIA is looking for subject matter expertise in the delivery of complex, foundational and novel Cybersecurity capability.
This contract is to provide consistent support on a deliverable-based (completion-type) contract, to NCSC contributing to its mission based on the deliverables that are described in the scope of work below.
3. PURPOSE
The NCSC is responsible to defend NATO networks on a 24/7 basis and to share relevant cyber information with all its stakeholders. To achieve these objectives, it requires a significant amount of coordination and decision making within and outside the boundaries of NCSC. In an effort to better capture the meeting minutes, share them efficiently with the stakeholders and track decision that are made in such meetings, the NCSC is seeking support from industry. This Statement of Work (SoW) defines the expectations for this support to materialize.
The current expectation is that there will be one to several meetings to support on a daily basis, during weekdays.
4. SCOPE OF WORK
The aim of this SOW is to support NCSC with technical expertise specifically related to the operation and maintenance of Continuous Vulnerability Assessment (CVA) Analyst Support with a deliverable-based contract to be executed in 2025.
This task includes data analysis and reporting of data reported by the Continuous Vulnerability Assessment (CVA) Analyst Support. For the provision of consistent support and the execution of the task, NCIA will get subject matter expertise from the industry with a service (deliverable based/completion type) based AAS framework contract in the delivery of requested capability.
The Cyber Continuous Vulnerability Assessment (CVA) Support gives visibility and insight on the networks in NATO environment, which in turn is critical to effective management, strong security and compliance, and efficient migrations and consolidations.
More broadly, NATO needs to be able to monitor the configuration of its domain controllers in order to prevent exploitation by malicious threat actors.
Under the direction / guidance of the NCSC Point of Contact, a contractor will be the part of the NCSC Team supporting the following activities:
1) Monitoring and Reporting :
a) Proactively review logs and alerts to identify any technical issues, errors, or failures in the monitoring process,
b) Produce and distribute reports related to system health, monitoring activities, and compliance status (e.g., audit logs, system performance metrics).
2) System Documentation:
a) Document configuration and changes: Keep up-to-date documentation of all configurations, integration steps, troubleshooting procedures, and system maintenance tasks,
b) Maintain an inventory: Keep track of all integrated identity sources, IAM systems, and external tools.
3) Automation and Scripting
a) Improve system efficiency: Identify areas where automation could reduce manual intervention and improve operational efficiency.
Activity A1: Under the direction of the NCSC Continuous Vulnerability Assessment Head the contractor shall deliver the following:
• Daily: Verify that the Continuous Vulnerability scans are configured correctly and that information collected is accurate & complete.
• Daily: Identify possible scan gaps, authentication failures and engage with relevant service provider to remove those gaps and eliminate reasons for authentication failure.
• Daily: Review existing scan policies, fine tune and improve them at the same time.
Activity A2:
• Weekly: Upon completion of scheduled scans, deliver a comprehensive vulnerability report to each stakeholder under you area of responsibility taking into account all vulnerabilities posing a security risk, remediation actions recommended to the system/application owners and the status of the recommended actions.
The weekly report is expected to be delivered each Wednesday/Thursday before Close of Business.
• No weekly report is due if that week does not include any working day (for instance: long official holidays such as Christmas break).
Activity A3:
• Monthly: deliver vulnerability report to stakeholders, with an overview of the critical/high vulnerabilities identified, the status of the recommended actions to show in a graphic way the trend of the security posture of CIS assets. The monthly report is expected to be delivered in the week of Microsoft patch Tuesday (second Tuesday of the month).
The measurement of execution for this work is sprints. The Contractor will provide services related to the activities above, using an agile and iterative approach using multiple sprints, with each sprint planned for a duration of 5 working days.
Due to the AGILE approach of this project, there is a need to define a set of specific arrangements between the NCIA and the contractor that specifically defines the deliverables to be provided for each sprint as well as their associated acceptance criteria. This includes sprint planning, execution and review processes, which are detailed below:
1. Sprint Planning:
Objective: Plan the objectives for the upcoming sprints.
Kick-off meeting: Conduct a monthly meeting with the contractor to plan the objectives of upcoming sprints and review contractor’s manpower to meet the agreed deliverables.
Set sprint goals: Define clear, achievable goals for the sprint and associated acceptance criteria, including specific delivery targets, Quality standards as well as Key Performance Indicators (KPIs) for each task to be recorded in the sprint meeting minutes.
Agree on the required level of effort for the various sprint tasks.
Backlog Review: Review and prioritise the backlog of tasks, issues, and improvements from previous sprints.
Assess each payment milestone cycle duration of 1 calendar month. State of completion and validation of each sprint status and sign off sprints to be submitted for payment as covered in Section 4.
There should be a sprint planning meeting every 4 sprints, that is 4 calendar weeks.
2. Sprint Execution
Objective: Contractor to execute the agreed “sprint plans” with continuous monitoring and adjustments.
Regular meetings between NCIA and the contractor to review sprint progress, address issues and make necessary adjustments to the processes or production methodology. The Meetings will be physically in the office, or in person via electronic means using Conference Call capabilities, according to the NCIA project manager’s instructions.
Continuous improvement: Contractor to establish a continuous feedback loop to gather input from all stakeholders for ongoing improvements and their subsequent implementation depending on NCIA approval.
Progress Tracking: Contractor to use a shared dashboard or tool to track the status of the sprint deliveries and any issues.
Quality Assurance/Quality Check: Contractor shall ensure that the quality standards agreed for the sprint deliverables are maintained throughout the sprint.
Quality Control: NCIA to perform the Final Quality Control of the agreed deliverables and provide feedback on any issues.
3. Sprint Review
Objective: Review the sprint performance and identify areas for improvement.
At the end of each sprint, there will be a meeting between the NCIA and the Contractor to review the outcomes against the acceptance criteria comprising sprint goals, agreed quality criteria and Key Performance Indicators (KPIs).
Define specific actions to address issues and enhance the next sprint.
4. Sprint Payment
For each sprint to be considered as complete and payable, the contractor must report the outcome of their work during the sprint, first verbally during the retrospective sprint review meeting and then in writing within three days after the sprint’s end date. A report must be sent by email to the NCIA Core GIS Senior Service Delivery Manager, listing all the work achieved against the agreed tasking list set for the sprint.
The contractor's payment for each sprint will be depending upon the achievement of agreed Acceptance Criteria for each task, defined at the sprint planning stage. This will include specific delivery targets, quality standards as well as Key Performance Indicators (KPIs) for each task.
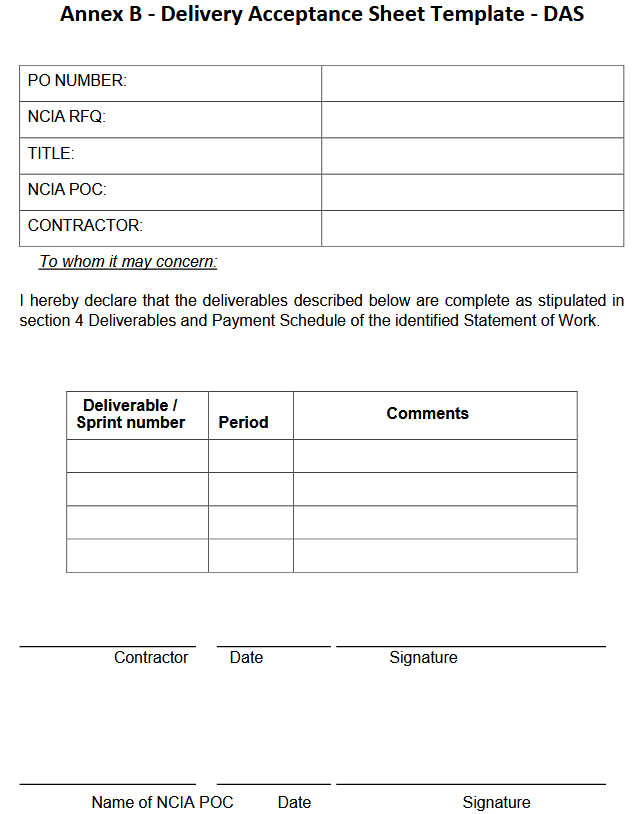
The payment shall be dependent upon successful acceptance as set in the above planning/review meetings. This will follow the payment milestones that shall include a completed Delivery Acceptance Sheet (DAS) – (Annex B).
Invoices shall be accompanied with a Delivery Acceptance Sheet (DAS) – (Annex B) signed by the Contractor and project authority.
If the contractor fails to meet the agreed Acceptance criteria for any task, the NCIA reserves the right to withhold payment for that task/sprint.
5. DELIVERABLES AND PAYMENT MILESTONES
The following deliverables are expected from this statement of work:
1. Complete the activities/tasks agreed in each sprint meeting as per section 4 above
2. Produce sprint completion reports (format: e-mail update) or the formal documentation required per specific task
3. The contractor will participate in the daily reporting and planning activities (daily stand-ups) as well as the required participation in workshops, events and conferences related to the supported services, as requested by the service delivery manager.
4. Payment schedule will be according to the payment milestones upon completion of the respective sprint. Upon completion and validation of each sprint and at the end of the monthly milestone, following the acceptance of the sprint report.
5. The NCIA team reserves the possibility to exercise a number of options, based on the same deliverable timeframe, later, depending on the project priorities and requirements. Each deliverable shall accurately reflect what was discussed, decided, and action items assigned. Sensitive information discussed prior, during and after meetings shall be handled in accordance with the NATO policy on Information Management.
6. The payment shall be dependent upon successful acceptance of the sprint report and the Delivery Acceptance Sheet (DAS) – (Annex B).
7. Invoices shall be accompanied with a Delivery Acceptance Sheet (Annex A) signed by the Contractor and the NCIA POC.
Deliverable: 10 sprints to support NCSC Assess Branch with Continuous Vulnerability Assessment (CVA) Analyst as per described in Para 4 (Number of sprints is estimated and will be adjusted based on actual starting date.)
Payment Milestones: Payment Schedule will be monthly for the completed and accepted sprints within the month and at the end of the work. Completion of each payment milestone shall be accompanied by a DAS signed for acceptance by the Purchaser’s authorized point of contact.
2026, 2027 and 2028 Options: 1 January to 31 December:
Deliverable: 46 sprints to support NCSC Assess Branch with Continuous Vulnerability Assessment (CVA) Analyst as per described in Para 4
Cost Ceiling: Price will be determined by applying the price adjustment formula as outlined in CO‐115786‐ AAS+ Special Provisions article 6.5.
Payment Milestones: Payment Schedule will be monthly for the completed and accepted sprints within the month and at the end of the work. Completion of each payment milestone shall be accompanied by a DAS signed for acceptance by the Purchaser’s authorized point of contact.
Each deliverable shall meet the following requirements:
• Language: the product shall be written in English, meeting or exceeding the NATO STANAG 6001 Level 3 “Professional Proficiency”.
• Intended Audience: the product shall be intended for Cyber Security Professional, Senior Military personnel and decision makers in the field of Cyber Security and Cyberspace Operations.
• Accuracy: the product shall accurately reflect what was discussed, decided, and action items assigned during the meeting.
• Clarity and Conciseness: Information shall be presented clearly and concisely, avoiding unnecessary jargon or complex language.
• Objectivity: the content shall be impartial and objective, presenting information without bias or personal interpretation.
• Structure: the product shall follow a logical structure, typically including sections such as agenda, attendees, discussions, decisions, action items, and any other relevant information, further directed by the IKM SG.
• Timeliness: the product shall be prepared and distributed promptly after the meeting, ensuring that information is fresh and actionable. It is expected a maximum of two times the length of the meeting for the time required to prepare and share the product to the meeting audience for initial review.
• Formatting: Consistent formatting shall be used throughout the document, including font style, size, headings, and spacing further directed by the IKM SG.
• Confidentiality: Sensitive information discussed prior, during and after meetings shall be handled in accordance with the NATO policy on Information Management.
6. COORDINATION AND REPORTING
The contractor shall participate in daily status update meetings, activity planning and other meetings as instructed, physically in the office, or in person via digital means using conference call capabilities, according to the manager’s / team leader’s instructions.
For each sprint to be considered as complete and payable, the contractor must report the outcome of his/her work during the sprint, first verbally during the retrospective meeting and then in written within three (3) days after the sprint’s end date. The format of this report shall be a short email to the NCIA Service Delivery Manager mentioning briefly the work held and the development achievements during the sprint.
At the end of the project, the Contractor shall provide a Project Closure Report that is summarizing the activities during the period of performance at high level.
7. ACCEPTANCE AND REJECTION CRITERIA
a) Acceptance Criteria
a.1. Quality of work reached NATO standards
a.2. Tasks are completed within the assigned time, as agreed in the sprint planning
a.3. Performances are as defined by the line manager as agreed in the sprint planning
a.4. Accuracy: the product shall accurately reflect what was discussed, decided, and action items assigned during weekly meeting per sprint.
a.5. Clarity and Conciseness: Information shall be presented clearly and concisely, avoiding unnecessary jargon or complex language.
a.6. Objectivity: the content shall be impartial and objective, presenting information without bias or personal interpretation.
a.7. Structure: the product shall follow a logical structure, typically including sections such as agenda, attendees, discussions, decisions, action items, and any other relevant information, further directed by the IKM SG.
a.8. Timeliness: the product shall be prepared and distributed promptly after the meeting, ensuring that information is fresh and actionable. It is expected a maximum of two times the length of the meeting for the time required to prepare and share the product to the meeting audience for initial review.
a.9. Formatting: Consistent formatting shall be used throughout the document, including font style, size, headings, and spacing further directed by the IKM SG.
a.10. Confidentiality: Sensitive information discussed prior, during and after meetings shall be handled in accordance with the NATO policy on Information Management.
b) Rejection Criteria
b.1. Quality of work is low
b.2. Tasks are not completed within the assigned time
b.3. Performances are not as defined by the line manager
c) A replacement will be requested if the contractor cannot fulfil the tasks as explained in rejection criteria.
d) Payment will not be done if the sprint is not completed.
8. PENALTY AND REJECTION PROCESS
If the contractor’s personnel does not meet the level of service expected based on the CV presented, the assigned tasks are not delivered as expected based on NATO standards or the finalization of the assigned tasks are not done within the given time, the sprint will not be accepted and the service will not be paid.
If any of the above-mentioned issues persist, the contractor will be asked to provide a replacement.
9. SCHEDULE
This task order will be active immediately after signing of the contract by both parties.
The period of performance is as soon as possible but not later than 20 October 2025 and will end no later than 31 December 2025.
10. CONSTRAINTS
All the deliverables provided under this statement of work will be based on NCIA templates or agreed with the project point of contact.
All documentation etc. will be stored under configuration management and/or in the provided NCIA tools.
11. SECURITY AND NON-DISCLOSURE AGREEMENT
It is mandatory to have the candidate be in possession of a COSMIC TOP SECRET security clearance to facilitate follow-on engagements and coordination at NATO venues.
The signature of a Non-Disclosure Agreement between the contractor contributing to this task and NCIA will be required prior to execution.
12. PRACTICAL ARRANGEMENTS
The contractor will be required to work onsite in Mons / BEL as part of this engagement. The NCSC Team is located in Mons / BEL, with working hours to be adjusted accordingly.
The services will be mainly executed on premise in SHAPE, Mons, Belgium. NCIA IT equipment will be provided (NCSC NROP laptop & NCSC NSOP workstation).
Results of the work will be provided on a weekly basis to the assigned Point of Contact (Annex A – weekly action tracking report).
The contractor will be required to work within a NATO country, following the rules and regulations applicable for the operations of NATO CIS.
The contractor will not be required to travel to other NATO locations as part of his role.
Travel expenses for missions to other NATO/NCIA locations: No travel expected. Daily presence on SHAPE, Mons Belgium is expected to deliver according to performance goals.
Regular travel costs to and from main location of the work (SHAPE, Mons, Belgium) are out of scope and will be borne by the contractor.
This work must be accomplished by one contractor for the entire duration of the contract.
The Purchaser will provide the contractor with the following Purchaser-Furnished Equipment (PFE):
• Access to NATO sites, as required, for the purpose of executing this SOW.
• Workspace (needed business IT for both on- and off-site work, hot-desk at NCSC facility).
• NCIA “REACH” laptop to be used by the contractor for the execution of the contract.
13. REQUIREMENTS
[See Requirements]
Requirements
11. SECURITY AND NON-DISCLOSURE AGREEMENT
- It is mandatory to have the candidate be in possession of a COSMIC TOP SECRET security clearance to facilitate follow-on engagements and coordination at NATO venues.
13. REQUIREMENTS
The contractor(s) that is going to deliver the identified services must have demonstrated skills, knowledge and experience as listed below:
MANDATORY:
- Bachelor's degree in Computer Science, Information Technology, or related field Or equivalent experience
- Minimum of 3 years’ experience required for all listed technical qualifications unless otherwise specified.
- 3+ years of professional experience in IT security, specifically in Vulnerability Assessment and / or Security Audit of large organisation
- Strong understanding of security best practices and hands-on experience with Tenable products especially with Tenable Security Center and Tenable Nessus Agent Manager (minimum 3 years)
- Strong knowledge and hands-on in SQL database scripting and Power BI (3+ years of hands-on experience)
- Strong knowledge of python (pyTenable) and PowerShell (3+ years experience required)
- Experience working with Tenable Security Center and Nessus Agent Manager APIs (3+ years experience)
- In-depth knowledge in Windows Domain environment (Active Directory structure, Tiers Model, LAPS, Group Policy Objects, DNS)
- Basic knowledge of Unix / Linux OS
- Strong analytical and problem-solving skills
- Excellent communication and collaboration skills
- Ability to understand and interpret the outcomes of security audit reports
DESIRABLE:
The candidate should also ideally have knowledge and experience in the following areas:
- Experience in working with NATO.
- Experience of working with NATO Communications and Information Agency.
- Experience of working with national Defence or Government entities.
- Experience with threat intelligence, incident response and remediation a plus
- Knowledge of NATO organization and its IT infrastructure is a plus
- Certifications such as CISSP, CISM, or CISA is a plus
- Previous experience working for Cyber Security related organisations (CERTs, security offices) is a plus
- Previous experience working in an international environment comprising both military and civilian elements is a plus (minimum 1 year, out of 3+ years of working in IT Security with a focus on Vulnerability Assessment and / or Security Audit on International environment)






